REST API Authentication Methods
Authentication in REST APIs is crucial for verifying the identity of a user or application trying to access an API. There are several methods available, each suited for different types of applications and security requirements.
- Basic Authentication
- Token-Based Authentication (Bearer Tokens)
Basic Authentication
Overview: Basic Authentication involves sending the username and password encoded in Base64 format within the request's header.
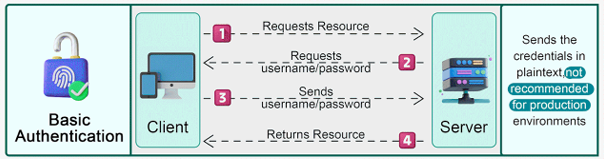
How it works:
- The client sends a request with an "Authorization" header.
- The header contains the word "Basic" followed by a space, then the base64-encoded "username:password" combination.
GET /api/data HTTP/1.1
Host: api.example.com
Authorization: Basic YWRtaW46cGFzc3dvcmQxMjM=
Content-Type: application/json
In this example:
- The username is admin and the password is password123.
- These credentials are Base64-encoded as YWRtaW46cGFzc3dvcmQxMjM=.
- The "Authorization" header carries the encoded credentials in the format: Authorization: Basic ;.
Advantages: Simple and easy to implement.
Disadvantages:
- Credentials are exposed in every request, making it vulnerable to interception.
- Should always be used over HTTPS for security.
Token-Based Authentication (Bearer Tokens)
Overview: Token-based authentication is a stateless authentication mechanism where a client (user or service) sends credentials
(e.g., username and password) to a server, and if validated, the server responds with a token (usually a JWT or JSON Web Token).
The client then uses this token in subsequent requests for authentication.
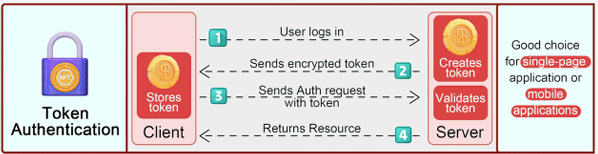
How it works:
- The client first authenticates using credentials and receives a token in response.
- The token is then included in the "Authorization" header of subsequent API requests.
- Request Token from Authentication Server (Login to get the token)
POST /api/login HTTP/1.1
Host: api.example.com
Content-Type: application/json
{
"username": "admin",
"password": "password123"
}
- After a successful login, the server will return a Bearer Token. For example:
{
"token": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9"
}
- Authenticated Request using the Bearer Token
GET /api/data HTTP/1.1
Host: api.example.com
Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9
Content-Type: application/json
Advantages:
- No need to send credentials with every request.
- Tokens can be stateless and self-contained (e.g., JWTs), meaning no need for server-side session storage.
Disadvantages:
- Tokens can expire or be revoked, requiring proper token management.
OAuth 2.0
Overview: OAuth (Open Authorization) is like giving a friend a key to your house so they can check on your pet while you're away,
but without giving them your house keys. Instead, you give them a temporary access key that allows them to enter your house only when needed.
This way, they can't access other parts of your house that they shouldn't, and they don’t need to know your private keys (like your actual house key).
How it works:
- The client requests an access token from an authorization server.
- The user or resource owner grants or denies permission.
- The authorization server returns an access token, which is then used in the "Authorization" header.
Advantages:
- Provides granular access control, allowing specific permissions for third-party applications.
- Commonly used in services like Google, Facebook, and GitHub for single sign-on (SSO).
Disadvantages:
- Complex setup compared to Basic or Token-based authentication.
- Requires managing access and refresh tokens.
4. API Key Authentication
Overview: API Key Authentication uses a unique key to identify the client.
How it works:
- The client includes the API key in either the query parameters or the request header.
- The API key is used by the server to authenticate and authorize the client.
Advantages:
- Simple to implement and easy for developers to use.
Disadvantages:
- API keys are less secure compared to OAuth or tokens since they do not expire and are often hard-coded into applications.
- API keys lack fine-grained access control.
5. HMAC Authentication (Hash-Based Message Authentication Code)
Overview: HMAC Authentication involves hashing both the request and a shared secret key to generate a signature. This signature is then sent with the request to prove its authenticity.
How it works:
- The client computes a hash using a secret key and message body.
- The hash is sent in the "Authorization" header along with the request.
- The server validates the hash using its own version of the shared secret.
Advantages:
- Ensures message integrity and authentication.
Disadvantages:
- More complex to implement.
- Requires both client and server to maintain a shared secret key.
6. Digest Authentication
Overview: Digest Authentication improves upon Basic Authentication by using a challenge-response mechanism where credentials are never sent directly over the network.
How it works:
- The server sends a nonce (a random number) to the client.
- The client responds with a hashed combination of the password and nonce.
Advantages: More secure than Basic Authentication, as passwords are not exposed in plain text.
Disadvantages:
- More complex than Basic Authentication.
- Can still be vulnerable to replay attacks if nonces are not handled properly.
7. Mutual SSL/TLS Authentication
Overview: Mutual SSL/TLS Authentication uses digital certificates to authenticate both the client and the server.
How it works:
- Both the client and server present SSL certificates to authenticate each other during the connection.
- This method uses encryption to ensure the confidentiality and integrity of the communication.
Advantages:
- Very secure, with strong encryption and two-way authentication.
Disadvantages:
- Requires both client and server to manage digital certificates, which can be complex.

