TCP Protocol Overview
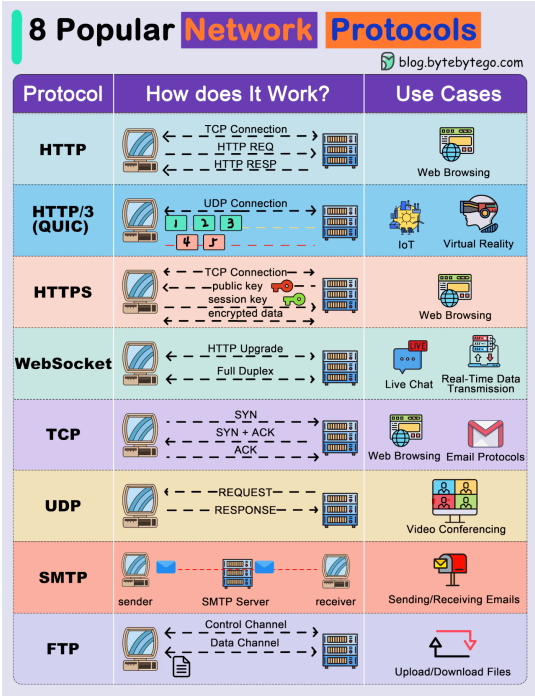
TCP, or Transmission Control Protocol, is indeed a fundamental protocol for many networked applications, including distributed systems and HTTP. It operates at the transport layer of the Internet Protocol Suite and is known for its reliability and robustness.
TCP is a connection-oriented protocol that establishes a connection between the sender and receiver before data transmission begins. This connection ensures that data is sent and received reliably, in the correct order, and without errors.
Reliable:
- TCP ensures that data sent from the sender is reliably received by the receiver. It uses a mechanism known as acknowledgments and retransmissions to achieve this.
Ordered:
- TCP guarantees that packets arrive in the same order they were sent. This is crucial for applications where the sequence of data is important.
Error-Checked:
- Each TCP packet includes a checksum that is used to verify the integrity of the data. When a packet arrives at its destination, the receiver calculates the checksum and compares it to the one sent with the packet. If there is a mismatch, it indicates that the packet was corrupted, and the receiver will request a retransmission.
UDP Protocol Overview
UDP, or User Datagram Protocol, is a lightweight and faster alternative to TCP. Unlike TCP, UDP is connectionless, which means it doesn’t establish a formal connection between sender and receiver before transmitting data. Let’s explore some of the characteristics of UDP based on the points you've provided:
- No Acknowledgment (No ACK): Unlike TCP, UDP does not use acknowledgments. Once the data is sent, there’s no confirmation from the receiver that the packet has arrived. The sender simply continues transmitting without waiting for feedback.
- No Ordering or Corruption Checking: UDP does not guarantee that packets will arrive in order or even intact. If packets are dropped, arrive out of sequence, or get corrupted during transit, UDP does not attempt to correct these issues. It’s up to the application to handle this if necessary.
- Fast: UDP’s lack of features like acknowledgment and retransmission makes it much faster than TCP. Since there’s no overhead for ensuring reliable delivery or ordering, data can be sent more quickly.
- Unreliable: UDP is considered unreliable because it doesn’t check whether the data has arrived or whether it’s arrived in the correct order. Data loss is possible, and there are no guarantees of delivery.
- Faster Than TCP: UDP is generally faster than TCP because it allows the sender to transmit large amounts of data quickly without waiting for acknowledgments or ensuring reliability. This is especially useful in applications where some data loss is acceptable for the sake of speed.
In a stock exchange application, data needs to be sent quickly, even if some data packets are lost in transit. Similarly, for video streaming or online gaming, minor data losses may not significantly impact the user experience, so speed is prioritized over reliability.
Common Use Cases
UDP is commonly used in scenarios where speed is critical, and a small amount of data loss is tolerable:
- Stock Exchanges: High-frequency trading requires real-time data delivery where speed is more important than reliability.
- Video Streaming: UDP allows for fast delivery of video packets, and minor losses or out-of-order packets can be handled by the application.
- Online Gaming: In fast-paced multiplayer games, slight delays or packet loss can be tolerated for the sake of maintaining game speed and responsiveness.
What is HTTP/HTTPS?
- HTTP (Hypertext Transfer Protocol):
- An application-layer protocol used for transmitting hypermedia documents, such as HTML.
- HTTP is the foundation of data communication on the World Wide Web.
- It is a stateless protocol, meaning each request from a client to server is independent, and the server does not retain user state between requests.
- HTTPS (Hypertext Transfer Protocol Secure):
- An extension of HTTP, where communication between the client and server is encrypted using TLS (Transport Layer Security) or SSL (Secure Sockets Layer).
- HTTPS ensures the confidentiality, integrity, and authenticity of data exchanged between the client and server.

How HTTP/HTTPS Works?
- HTTP:
- The client (usually a web browser) sends an HTTP request to the server, typically requesting a resource like a web page.
- The server processes the request and sends back an HTTP response, which usually contains the requested resource (e.g., an HTML file, image, etc.).
- HTTP operates over TCP (Transmission Control Protocol), usually on port 80.
- HTTPS:
- HTTPS follows the same process as HTTP, but before data is sent, the client and server establish a secure connection using SSL/TLS.
- This secure connection ensures that the data exchanged is encrypted, preventing eavesdropping and tampering.
- HTTPS typically operates over port 443.
Why HTTP/HTTPS is Used?
- HTTP:
- To request and receive web resources such as HTML pages, images, and other multimedia content.
- Facilitates communication between web browsers and servers on the internet.
- Supports various methods like GET, POST, PUT, DELETE, etc., to interact with resources on the server.
- HTTPS:
- To secure data transmission between clients and servers, protecting sensitive information (e.g., login credentials, payment details).
- Ensures that the data exchanged is not intercepted, tampered with, or forged by attackers.
- Provides authentication to confirm the identity of the communicating parties.
Where HTTP/HTTPS is Used?
- HTTP:
- Standard websites where security is not a major concern (e.g., public information sites, blogs).
- APIs and services that do not handle sensitive data.
- HTTPS:
- Websites that handle sensitive data (e.g., banking sites, e-commerce platforms, login pages).
- APIs and services that require data integrity and confidentiality.
- Websites that need to comply with security standards and regulations (e.g., PCI-DSS for payment processing).
HTTP Methods and Status Codes
HTTP Methods
| Method | Description |
|---|---|
| GET | Used to request data from a specified resource. It’s a read-only operation and does not modify the resource. |
| POST | Used to send data to the server, usually to create or update a resource. Commonly used in form submissions. |
| PUT | Used to update an existing resource or create a new resource if it doesn’t exist. |
| DELETE | Used to delete a specified resource. |
| PATCH | Used for partial updates to a resource. |
| HEAD | Same as GET, but the server only returns headers without the body content. |
| OPTIONS | Used to describe the communication options for the target resource. It returns allowed HTTP methods for that resource. |
HTTP Status Codes
| Status Code | Class | Description |
|---|---|---|
| 100 | 1xx Informational | Continue - The server has received the request headers and the client can proceed to send the body. |
| 101 | 1xx Informational | Switching Protocols - The server agrees to switch protocols as requested by the client. |
| 200 | 2xx Success | OK - The request was successful, and the server returned the requested data. |
| 201 | 2xx Success | Created - The request was successful, and a new resource was created. |
| 204 | 2xx Success | No Content - The request was successful, but there is no content to send in the response. |
| 301 | 3xx Redirection | Moved Permanently - The requested resource has been permanently moved to a new URL. |
| 302 | 3xx Redirection | Found - The requested resource has been temporarily moved to a new URL. |
| 304 | 3xx Redirection | Not Modified - The requested resource has not been modified since the last request. |
| 400 | 4xx Client Error | Bad Request - The server could not understand the request due to invalid syntax. |
| 401 | 4xx Client Error | Unauthorized - The request requires user authentication. |
| 403 | 4xx Client Error | Forbidden - The server understood the request, but it refuses to authorize it. |
| 404 | 4xx Client Error | Not Found - The requested resource could not be found on the server. |
| 500 | 5xx Server Error | Internal Server Error - The server encountered an error while processing the request. |
| 502 | 5xx Server Error | Bad Gateway - The server, while acting as a gateway, received an invalid response from the upstream server. |
| 503 | 5xx Server Error | Service Unavailable - The server is currently unable to handle the request due to temporary overload or maintenance. |
SSL/TLS
- SSL (Secure Sockets Layer):
- SSL is a standard security technology for establishing an encrypted link between a server and a client—typically a web server (website) and a browser or a mail server and a mail client (e.g., Outlook).
- TLS (Transport Layer Security):
- TLS is the successor to SSL and is more secure and efficient.
- It is a cryptographic protocol designed to provide secure communication over a computer network.
SSL/TLS Handshake Process (In-Depth)
- Step 1: Client Hello
- The client initiates the handshake by sending a "Client Hello" message, which includes the SSL/TLS version it supports, the list of encryption algorithms, and a randomly generated number.
- Step 2: Server Hello
- The server responds with a "Server Hello" message, selecting the encryption algorithm from the list provided by the client and sending its SSL/TLS certificate. This certificate contains the server's public key.
- Step 3: Server Certificate and Key Exchange
- The server sends its SSL/TLS certificate, and if required, a "Server Key Exchange" message. The client verifies the certificate to ensure the server's authenticity.
- Step 4: Client Key Exchange
- The client generates a "pre-master secret," encrypts it with the server's public key, and sends it to the server. Both client and server use this pre-master secret to generate the session keys used to encrypt the data.
- Step 5: Finished Messages
- Both the client and server send a "Finished" message, encrypted with the session key, indicating that the handshake is complete and a secure session is established.
- Step 6: Secure Communication
- All subsequent communication between the client and server is encrypted using the session keys established during the handshake.